
What the HPE Aruba Private 5G Core Vulnerability Means for Your Private Cellular Network and How to Stay Protected
If you manage or secure a private cellular network, the latest vulnerability disclosure from HPE Aruba Networking should be a wake-up call. HPE Aruba Networking has announced a high-severity ...
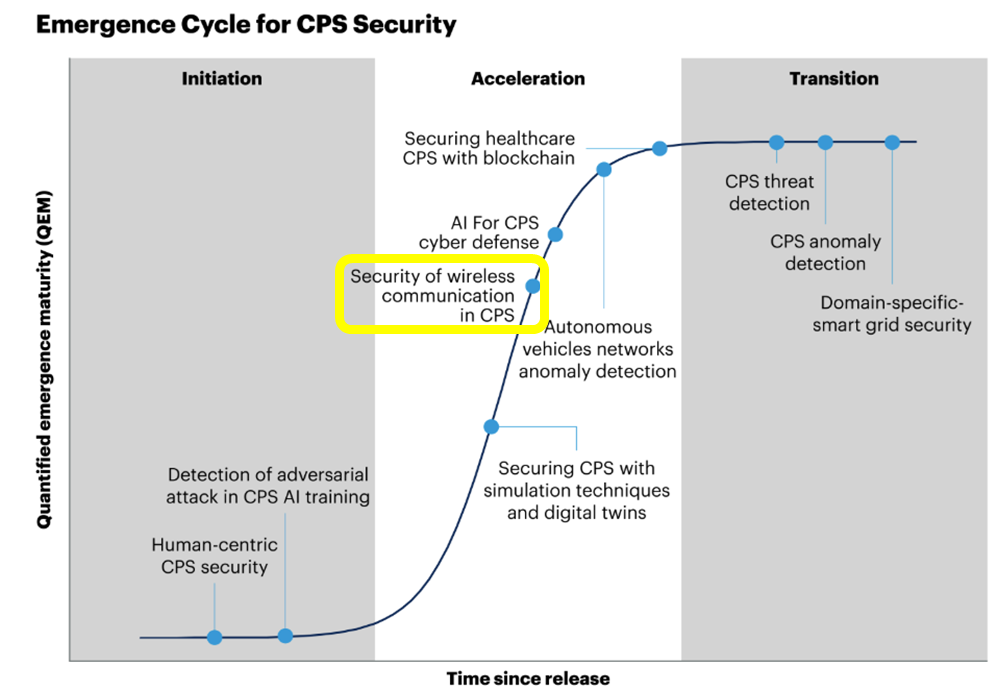
OneLayer Named a Sample Vendor in the 2025 Gartner® Report for Emerging Tech: Emergence Cycle for CPS Security
OneLayer is proud to have been named a Sample Vendor in the 2025 Gartner® Report for Emerging Tech: Emergence Cycle for CPS Security. Cyber-physical systems (CPS) come in many forms, from ...

What the SK Telecom Hack Should Teach You About Your Private Cellular Network Security
The past three weeks have been a bad time to be a cell phone user in South Korea. Well, not for every cell phone user. Only if you happen to be one of the 25 million customers of the leading ...

Navigating the Future of Private 5G Network Security: OneLayer’s Market View Echoes in Gartner’s Insights
As the adoption of private 5G networks gains momentum, enterprises are beginning to delve deeper into the complexities and security challenges associated with these advanced systems. A recent ...

Vulnerabilities in Private 5G/LTE: A Growing Threat Landscape
Private 5G/LTE networks are rapidly gaining popularity across various industries, offering enhanced connectivity, improved efficiency, and greater control over network infrastructure. However, as ...

CISA’s Communications Infrastructure Guidance: Three Steps Every Enterprise Should Take
The recently disclosed Salt Typhoon security incident , which is still sending shockwaves through the telecommunications and government sectors globally, highlights the critical role that mobile ...

What the Salt Typhoon Attack Means for Enterprises: An Interview with OneLayer Cellular Network Expert Ido Shaked
Salt Typhoon, a Chinese state-sponsored cyberattack that has compromised eight telecommunications providers in the U.S. and likely many more globally, exposed a stark reality for enterprises that ...

The Challenges (and Solutions!) of Implementing NIST Zero Trust Architecture in Private 5G/LTE Networks
In a few decades, “trust no one” has gone from thriller-movie warnings to mainstream cybersecurity advice. NIST SP 800-207 on Zero Trust Architecture is a required standard in some ...

OneLayer Named a Cool Vendor in the 2024 Gartner® Cool Vendors™ in CPS Security
“CIOs and IT leaders should use Gartner’s Cool Vendors research to proactively understand and exploit disruptive technologies. Cool Vendors can serve as an excellent resource for both ...

Private 5G for OT Critical Applications – How to Gain Trust?
As organizations increasingly adopt private 5G networks, especially for OT-critical applications such as SCADA-PLC communication or industrial ethernet (Profinet or Profibus), reliability and ...

Visibility Behind Cellular Router/CPE: Do’s and Don’ts
As enterprises integrate private 5G and LTE networks with their existing IT and OT infrastructure, the use of cellular routers/CPEs to connect non-cellular devices becomes essential. Choosing the ...

OneLayer is Thrilled to Announce that We Have Been Named a Sample Vendor in 2 Gartner Hype Cycles™
As a trusted advisor, Gartner plays a pivotal role in companies' strategic analysis of their technology portfolios. Our inclusion in 2 Hype Cycles not only reflects Gartner's confidence in ...

The Hype is Real – Private Mobile Networks Are Maturing Faster Than Expected!
The Hype is Real - Private Mobile Networks Are Maturing Faster Than Expected! At OneLayer, we've witnessed a rapid acceleration in the adoption of private mobile networks over the past year. ...

Private Cellular Networks for the Upstream Oil & Gas Industries: An Operations and Security Checklist
Private Cellular Networks for the Upstream Oil & Gas Industries: An Operations and Security Checklist As the world’s private consumers come to expect 5G connectivity, industrial consumers ...

The Paradigm Shift from SIM-Centric to Device-Centric: Boost Your Private Network Management
The Paradigm Shift from SIM-Centric to Device-Centric: Boost Your Private Network Management In the rapidly advancing landscape of enterprise LTE and 5G cellular networks, traditional ...

Cybersecurity Attacks in Private Cellular Networks – Watch Out for the Bad Sparrow!
Navigating the New Frontier of Cybersecurity in Cellular Private Networks: A Deep Dive into the Sparrow Attack Introduction to the Evolving Threat Landscape As the digital and physical ...

What is the preferred architecture for private cellular networks?
A tale of two networks: Which is the preferred private network architecture? More and more enterprises today are implementing private 5G and LTE networks alongside their existing IT and OT ...

How to scale your private 5G/LTE network from pilot to fully operational autonomous network
The fast-evolving landscape of private 5G/LTE networks showed a move last year toward operational networks after several years of pilots and trials. A new player now enters the picture: operation ...

Private APNs and Brute Force SMS Attack Risks
Many enterprises using public cellular networks do so via private APNs (access point names), which provide an exclusive gateway for the organization's data traffic between the public cellular ...
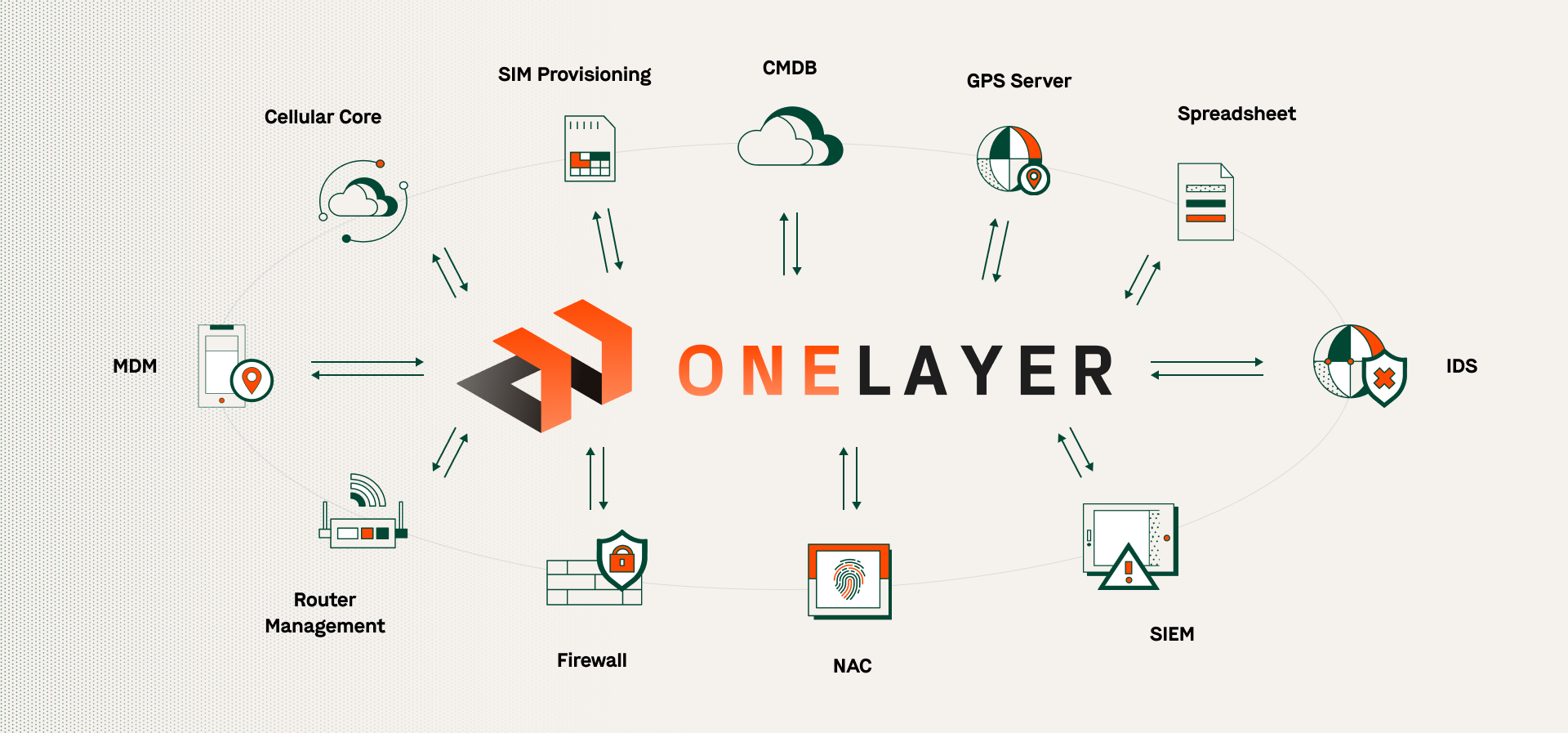
Creating an effective automated security ecosystem in private cellular: ingredients for success
Creating an effective automated security ecosystem in private cellular: ingredients for success Setting up and maintaining a private cellular network can feel like doing a jigsaw puzzle with ...

Bridging the Traceability Gap from Private Networks to Private APNs on Public Cellular Networks
OneLayer Introduces Seamless Integration of Private Networks with Private APNs on Public Cellular Networks OneLayer’s solution now supports use cases such as roaming or failover devices ...

Private cellular network segmentation: APNs are not enough!
Segmentation is a mandatory security practice in enterprise networks. As enterprises adopt private cellular networks, they look for effective segmentation solutions that align with their existing ...

OneLayer: Shaping the private cellular network revolution
When OneLayer was founded two years ago, private cellular networks were in operational infancy. It was early adopters and their innovation teams who were playing around with private LTE and 5G ...

Navigating the Cellular Labyrinth: IoT Asset Management in Private LTE/5G Networks
In today's digitally transformed landscape, IoT (Internet of Things) asset management plays a pivotal role in revolutionizing how organizations oversee and optimize their physical resources. At ...